Mobile security or mobile device security is the protection of smartphones tablets and laptops from threats associated with wireless computing. We secure your data with strong encryption and security best practices.

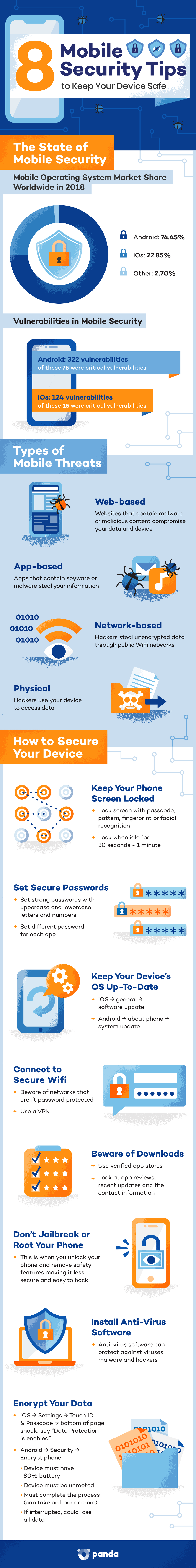
8 Mobile Security Tips To Keep Your Device Safe Panda Security
They turn any amount of data into a fixed-length fingerprint that cannot be reversed.
. On iOS go to Menu Security Checkup and on Android go to Menu Settings Security Checkup. During periods of contention these customers may experience reduced data speeds and increased latency as compared to other customers using. Millions of computers form a public network where communications can be intercepted.
The other reason for it can be the presence of erroneous data which prevents the camera app from working properly. Content Security Policy is an added layer of security that helps to detect and mitigate certain types of attacks including Cross-Site Scripting and data injection attacksThese attacks are used for everything from data theft to site defacement to malware distribution. This is called routing.
Keep in mind that disabling phone and SMS authentication affects authentication for all users no matter what mobile OS they use. Unauthorized users watch the keystrokes inputted on a device or listen to sensitive information being spoken which is also known as eavesdropping. It has become increasingly important in mobile computingThe security of personal and business information now stored on smartphones is of particular concern.
Test the Samsung Phones Camera in Safe Mode. So here are some easy ways to get rid of the Security Policy Prevents Use of Camera message from a Samsung smartphone. Restart the Samsung Phone.
Clear Cache Data for. The following table shows the types of security policies and what you can do with them. Kevin April 21 2022 at 402 pm I was experiencing the Security policy prevents use of camera message.
As data moves from sender to receiver it almost always has to travel through several other connections. Types of security policies. All infractions undergo a thorough review process by Activisions Tencents respective security teams before enforcement and penalties are not subject to further review.
For example the search result will probably point to the mobile page if the user is on a mobile device even if the desktop page is marked as canonical. To make your policy truly. You can use security policies with GKE and the default Ingress controller.
When we collect data we use it for a specific stated purpose to improve your experience and our service to you. Disable Device Admin Apps. In this increasingly digital era every business no matter the size has to be vigilant about its cybersecurity.
An alternative and far more secure method is always to use a mobile 4G5G connection through your own mobile device when possible. Security is the first and foremost requirement of Online banking because the Internet is inherently unsecured. Financial apps such as investing and banking commonly have screenshots disabled for security purposes.
Regardless of whether you share user data in your app if you collect and use it for ads purposes you need to declare the ads purposes in the Data safety section of the App content page in the Play Console. Hackers are always scheming to steal critical data and so it is best to stay ahead of the game. Creating an effective security policy and taking steps to ensure compliance is an important step towards preventing and mitigating security threats.
Containing 58 per cent of the world population in 2020 the EU generated a nominal gross domestic product GDP of around US171 trillion in 2021 constituting. More and more users and businesses use smartphones to communicate. Classify your information into personal or sensitive and label them accordingly.
One network management practice we use to manage our wireless network resources may affect customers with ATT post-paid and ATT PREPAID SM unlimited mobile data plans ATT Unlimited Data Plans. End users can always view their devices security posture from within the Duo Mobile app. Check Point endpoint security includes data security network security advanced threat prevention forensics endpoint detection and response EDR and remote access VPN solutions.
We respect local privacy laws and work with legal experts to stay abreast of changes. CSP is designed to be fully backward compatible except CSP version 2 where there are some explicitly-mentioned. Apps can access what data to prevent unnecessary security.
We will never use your data for targeted advertising. To offer simple and flexible security administration Check Points entire endpoint security suite can be managed centrally using a single management console. It prevents malicious code from being able to run in the background of your device and send a copy of your screen to a hacker.
A complete outline of the Call of Duty. Security Checkup notifies users about detected issues via a pop-up at the bottom of the app screen which they can tap to see more information. Tips to Fix Security Policy Prevents Use of Camera on Samsung.
Disable the Sensors Off Feature. Furthermore it is stopping the camera from working by taking the control of security policy permissions. Reasons for having similar or duplicate pages There are valid reasons why your site might have different URLs that point to the same page or have duplicate or very similar pages at different.
Some apps have a policy that prevents screenshots from being taken. Use the latest browser versions mobile OS and updated mobile applications to ensure they are patched against vulnerabilities and to use latest security features Exercise reasonable precautions while sharing data from our cloud environment. A check mark indicates that the type of security policy supports the feature.
Another related category is data security which focuses on protecting an organizations data from accidental or malicious exposure to unauthorized parties. 4 Methods To Fix. HTTP Strict Transport Security HSTS is a policy mechanism that helps to protect websites against man-in-the-middle attacks such as protocol downgrade attacks and cookie hijackingIt allows web servers to declare that web browsers or other complying user agents should automatically interact with it using only HTTPS connections which provide Transport Layer.
But at first you should find the third-party applications which are hindering the working of the camera. Use of the Advertising ID is mandatory for advertising use cases per the Google Play Developer Content Policy because the user can reset it. As I was running through the above trouble shooting steps I noticed that on the main settings pull down menu Sensors Off icon had been selected.
Return or destroy as applicable all Sensitive Data provided to the Vendor by Institution to Vendor including all Sensitive Data provided to Vendors employees subcontractors agents or other affiliated. These operating system sections and tables detail the state of our version data for the four major OS platforms as of June 9th 2021. Reason 3 Policy set in App.
Hash algorithms are one way functions. The European Union EU is a voluntary supranational political economic and monetary union of 27 democratic sovereign member states with social market economies that are located primarily in Europe. This data maps to the operating system policy options as.
Within 30 days after the termination or expiration of a Purchase Order Contract or Agreement for any reason Vendor shall either. Data breaches have become rampant over the past several years costing even the top companies millions of dollars in damages. They also have the property that if the input changes by even a tiny bit the resulting hash is completely different see the example above.
OS Specific Version Data. Mobile Security Enforcement Policy Below is Activisions posted Security Enforcement Policy for Call of Duty. In computer security shoulder surfing is a type of social engineering technique used to obtain information such as personal identification numbers PINs passwords and other confidential data by looking over the victims shoulder.

How To Fix Security Policy Prevents Use Of Camera On Samsung Phones

Enterprise Mobile Security Solutions Check Point Software
How To Fix Security Policy Prevent Use Of Mobile Data On Samsung Phones Techyloud

8 Mobile Security Tips To Keep Your Device Safe Panda Security

How To Secure Your Mobile Device In Six Steps
10 Ways To Fix Security Policy Prevents Use Of Camera On Samsung

How Do I Fix Security Policy Prevents Use Of Camera On All Samsung Galaxy Android Phone 2022 Youtube

Mobile App Security A Comprehensive Guide To Secure Your Apps Appsealing
0 comments
Post a Comment